BitLocker | Harden System Security¶
-

 The app sets up and configures BitLocker using official documentation, with the most secure configuration and military grade encryption algorithm, XTS-AES-256, to protect the confidentiality and integrity of all information at rest.
The app sets up and configures BitLocker using official documentation, with the most secure configuration and military grade encryption algorithm, XTS-AES-256, to protect the confidentiality and integrity of all information at rest.  CSP
CSP  CSP
CSP-
It offers 2 security levels for OS drive encryption: Enhanced and Normal.
-
In Normal security level, the OS drive is encrypted with TPM and Startup PIN. This provides very high security for your data, especially with a PIN that's long, complicated (uppercase and lowercase letters, symbols, numbers, spaces) and isn't the same as your Windows Hello PIN.
-
In Enhanced security level, the OS drive is encrypted with TPM and Startup PIN and Startup key. This provides the highest level of protection by offering Multifactor Authentication. You will need to enter your PIN and also plug in a flash drive, containing a special BitLocker key, into your device in order to unlock it. Continue reading more about it here.
-
Once the OS drive is encrypted, for every other non-OS drive, there will be prompts for confirmation before encrypting it. The encryption will use the same algorithm as the OS drive and uses Auto-unlock key protector. Removable flash drives are skipped.
-
The recovery information of all of the drives are saved in a single well-formatted text file in the root of the OS drive
C:\BitLocker-Recovery-Info-All-Drives.txt. It's very important to keep it in a safe and reachable place as soon as possible, e.g., in OneDrive's Personal Vault which requires additional authentication to access. See here and here for more info. You can use it to unlock your drives if you ever forget your PIN, lose your Startup key (USB Flash Drive) or TPM no longer has the correct authorization (E.g., after a firmware change). -
TPM has special anti-hammering logic which prevents malicious user from guessing the authorization data indefinitely. Microsoft defines that maximum number of failed attempts in Windows is 32 and every single failed attempt is forgotten after 2 hours. This means that every continuous two hours of powered on (and successfully booted) operation without an event which increases the counter will cause the counter to decrease by 1. You can view all the details using this PowerShell command:
Get-TPM. -
Check out Lock Screen category for more info about the recovery password and the 2nd anti-hammering mechanism.
-
BitLocker will bring you a real security against the theft of your device if you strictly abide by the following basic rules:
-
As soon as you have finished working, either Hibernate or shut Windows down and allow for every shadow of information to disappear from RAM within 2 minutes. This practice is recommended in High-Risk Environments.
-
Do not mix 3rd party encryption software and tools with BitLocker. BitLocker creates a secure end-to-end encrypted ecosystem for your device and its peripherals, this secure ecosystem is backed by things such as software, Virtualization Technology, TPM 2.0 and UEFI firmware, BitLocker protects your data and entire device against real-life attacks and threats. You can encrypt your external SSDs and flash drives with BitLocker too.
-
-
Important
AMD Zen 2 and 3 CPUs have a vulnerability in them, if you use one of them, make sure your BitLocker Startup PIN is at least 16 characters long (max is 20).
-
 Enables or disables DMA protection from BitLocker Countermeasures based on the status of Kernel DMA protection. Kernel DMA Protection is not compatible with other BitLocker DMA attacks countermeasures. It is recommended to disable the BitLocker DMA attacks countermeasures if the system supports Kernel DMA Protection (The Harden System Security App does that exactly). Kernel DMA Protection provides higher security bar for the system over the BitLocker DMA attack countermeasures, while maintaining usability of external peripherals. You can check the status of Kernel DMA protection using this official guide.
Enables or disables DMA protection from BitLocker Countermeasures based on the status of Kernel DMA protection. Kernel DMA Protection is not compatible with other BitLocker DMA attacks countermeasures. It is recommended to disable the BitLocker DMA attacks countermeasures if the system supports Kernel DMA Protection (The Harden System Security App does that exactly). Kernel DMA Protection provides higher security bar for the system over the BitLocker DMA attack countermeasures, while maintaining usability of external peripherals. You can check the status of Kernel DMA protection using this official guide.  CSP
CSP- Kernel DMA Protection (Memory Access Protection) for OEMs page shows the requirements for Kernel DMA Protection. for Intel CPUs, support for requirements such as VT-X and VT-D can be found in each CPU's respective product page. e.g. Intel i7 13700K
 Disallows standard (non-Administrator) users from changing the BitLocker Startup PIN or password
Disallows standard (non-Administrator) users from changing the BitLocker Startup PIN or password  CSP
CSP
-
 (Only on Physical machines) Enables Hibernate and adds Hibernate to Start menu's power options.
(Only on Physical machines) Enables Hibernate and adds Hibernate to Start menu's power options.  CSP
CSP- Devices that support Modern Standby have the most security because (S1-S3) power states which belong to the legacy sleep modes are not available. In Modern Standby, security components remain vigilant and the OS stays protected. Applying Microsoft Security Baselines also automatically disables the legacy (S1-S3) sleep states.
 Allow network connectivity during connected-modern-standby (only when plugged in). Keeps the Operating System and Microsoft Defender up to date while the device is Modern Standby capable and is plugged in (meaning it's not on battery).
Allow network connectivity during connected-modern-standby (only when plugged in). Keeps the Operating System and Microsoft Defender up to date while the device is Modern Standby capable and is plugged in (meaning it's not on battery).  CSP
CSP
Refer to this official documentation about the countermeasures of BitLocker
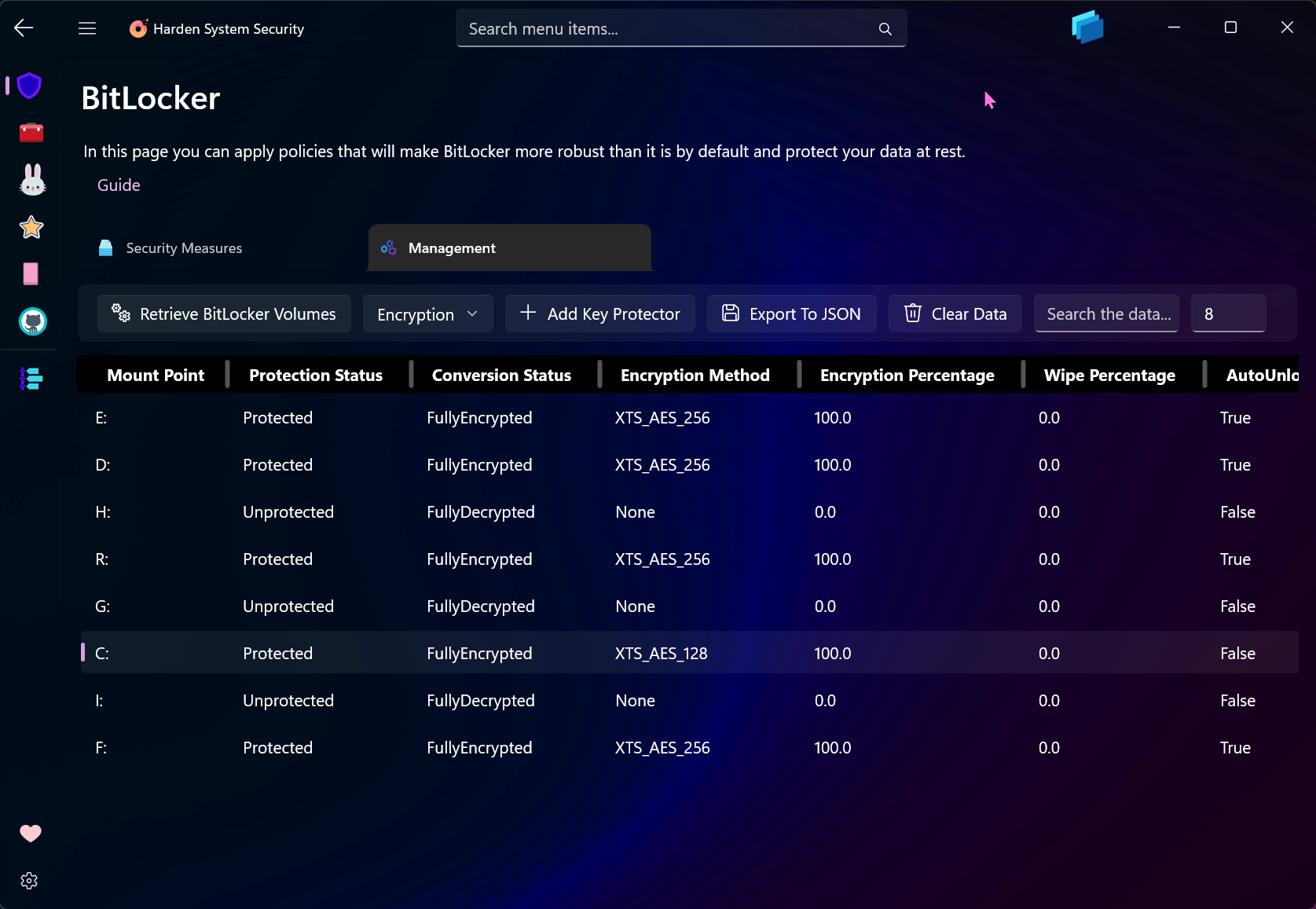
BitLocker Management¶
Full Drive Encryption¶
You can enable BitLocker encryption for the Operating System (OS) drive, fixed drives, and removable drives via a guided, safety-first workflow. All messages and UI elements related to BitLocker are localized for the languages supported by the app. BitLocker management is implemented in the low-level ComManager component of Harden System Security.
Add or Modify Key Protectors¶
A step-by-step workflow allows you to add and modify a variety of key protectors for BitLocker-protected volumes, making key management straightforward and auditable.
Suspend BitLocker Encryption¶
Need to update firmware or perform maintenance? Use the Suspend feature to temporarily suspend BitLocker protection on the OS drive. You may optionally specify the number of restarts after which protection will be automatically resumed.
Resume BitLocker Encryption¶
Quickly resume protection for drives whose BitLocker state was previously suspended.
Backup BitLocker Key Protectors¶
Back up recovery passwords and key protector details for your drives so you have access to the required 48-character recovery keys when needed.
After enabling BitLocker for a drive or adding a new Key Protector, the Export button will light up briefly, giving you a subtle reminder that it's best to export the data and back them up so you don't forget that.
Tip
Because BitLocker operations can be consequential, every action requires explicit confirmation before proceeding. Additionally, the preselected (focused) button in each confirmation dialog is Cancel to further reduce the chance of accidental acceptance.