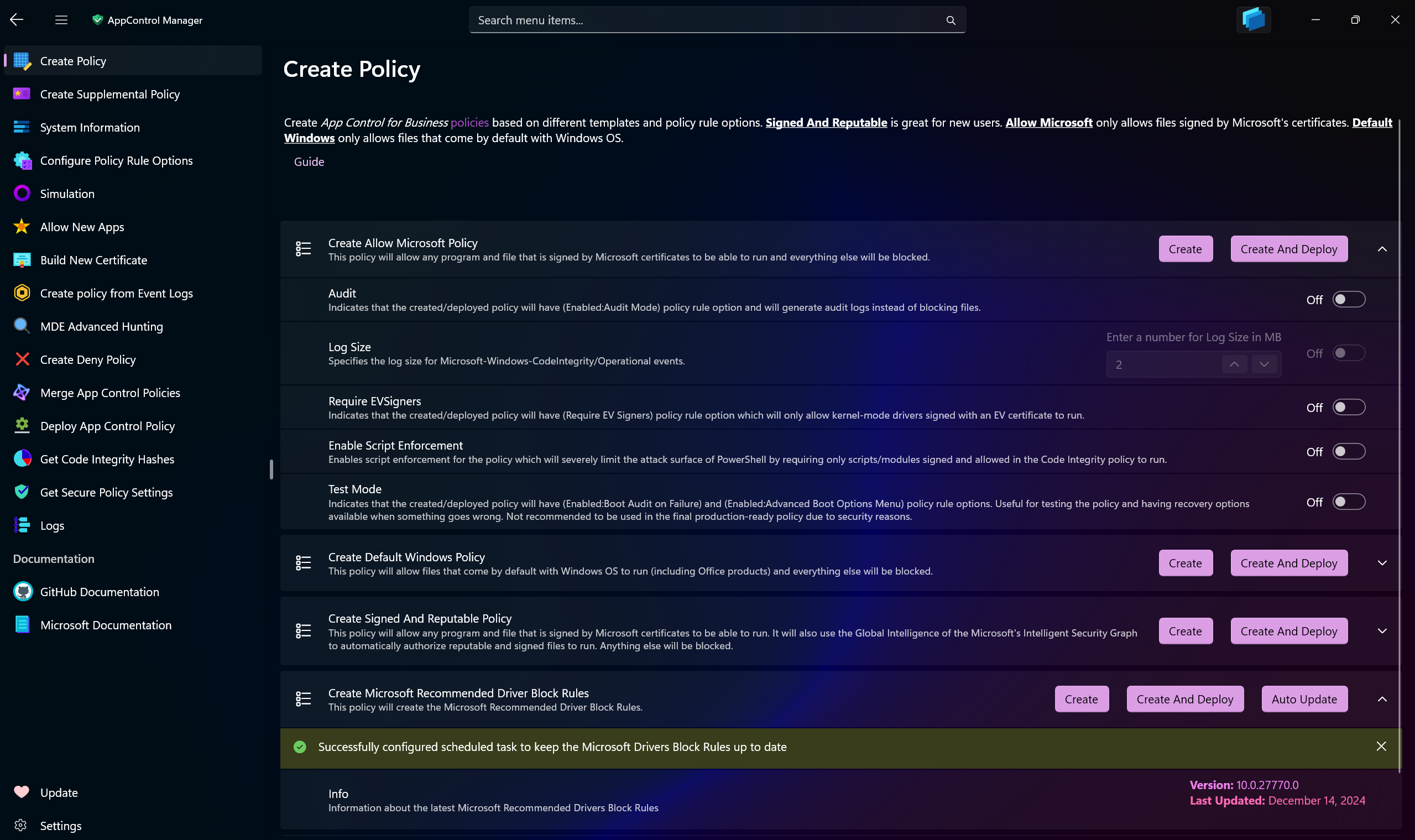
Create App Control Policy¶
Use AppControl Manager to create new App Control policies based on the default templates.
-
Allow Microsoft: Only allows files signed by Microsoft certificates to run on the system.
-
Default Windows: Only allows files that come by default with Windows OS to run on the system.
-
Signed And Reputable: Allows files signed by Microsoft certificates to run, it also utilizes the Intelligent Security Graph to allow files that are reputable and safe.
-
To effectively use this template, the system where it will be deployed must have reliable Internet connection to communicate with the ISG servers.
-
Microsoft Recommended Block Rules: It will download the latest Microsoft Recommended (User-Mode) block rules from the official source and create an App Control policy.
-
Microsoft Recommended Driver Block Rules: It will download the latest Microsoft Recommended (Kernel-Mode) block rules from the official source and create an App Control policy.
-
Auto update: It will create a scheduled task on the system that will check every week for the latest Microsoft Recommended block rules and update the policy automatically. Please refer to this page for more info.
-
Strict Kernel-mode policy: It's a special kind of policy that will only enforce Kernel-mode files without blocking user-mode files. Please refer to this article for more information.
Deploying any of them is optional. You can create the policies and then deploying them on remote systems using Intune or other methods.
Configuration Details¶
There are different settings and options you can use to fine tune the policy according to your requirements.
-
App ID Tagging Policy: When enabled, the policy that will be created will be an App ID Tagging policy type based on the selected template. It will have the same rules as the template you selected. It's only available for
Allow MicrosoftandDefault Windowstemplates. The created App ID Tagging policies will each have one default tag in them that areAllowMSFTTagKeyandAllowMSFTTagKeyrespectively with the value ofTrue. -
Audit: When a policy has Audit mode turned on for it, it will only log the events and not block any files from running.
-
Log Size: You can configure the max capacity of the
Code Integrity/Operationallog size. It is recommended to increase it from the default1MBcapacity if you want to begin auditing for App Control events. When the capacity is reached, the log will overwrite the oldest events. -
Require EVSigners: When this setting is enabled, the policy will only allow files signed by Extended Validation (EV) certificates to run on the system.
-
Enable Script Enforcement: When this setting is enabled, the policy will only allow PowerShell scripts or modules that are signed and their signing certificates are allowed in an App Control policy to run. This greatly reduces the attack surface from the Windows script hosts and is enabled by default.
-
Test Mode: Boot Options Menu, such as Safe mode, is disabled for all App Control policies by default. Using Test Mode will allow access to it. It will also automatically enable the
Auditmode for the policy in case of a failure in a driver that is critical to system boot. It's only recommended to use this setting in a test environment and not in production due to security reasons.
Downloads Defense Measures  ¶
¶
To combat the threat of more sophisticated malware, a preemptive measure is taken by creating and deploying an App Control policy on the system. This policy blocks the execution of executables and other potentially harmful file types in the Downloads folder.
This policy defends the system from malware that can launch itself automatically after being downloaded from the Internet and has the potential to protect against zero-click exploits. The user must ensure the file's safety and explicitly transfer it to a different folder before running it.
The App Control policy employs a wildcard pattern to prevent any file from running in the Downloads folder. Additionally, it verifies that the system downloads folder in the user directory matches the downloads folder in the Edge browser's settings. If there is a discrepancy, a warning message is displayed on the console.
Creates a custom App Control policy that blocks the execution of the following executables:
- wscript.exe
- mshta.exe
- cscript.exe
They are insecure, unsandboxed script hosts that pose a security risk.